The Science of Cryptojacking: Risks and Protections
- Understanding Cryptojacking and its Impact on Computers
- How Hackers Use Cryptojacking to Mine Cryptocurrency
- The Dangers of Cryptojacking for Individuals and Businesses
- Detecting and Preventing Cryptojacking Attacks
- Tools and Techniques to Safeguard Against Cryptojacking
- The Future of Cryptojacking: Evolving Threats and Security Measures
Understanding Cryptojacking and its Impact on Computers
Cryptojacking is a form of cyber attack where hackers use a victim’s computer to mine cryptocurrency without their knowledge or consent. This malicious activity can have a significant impact on computers, causing them to slow down, overheat, and consume more energy than usual. As a result, users may experience decreased performance, increased electricity bills, and even hardware damage.
One of the main dangers of cryptojacking is that it can go undetected for long periods, allowing hackers to profit at the expense of unsuspecting victims. In addition to the immediate effects on computers, cryptojacking can also compromise sensitive data and expose users to other forms of malware. Therefore, it is essential for individuals and organizations to be aware of the risks associated with cryptojacking and take steps to protect themselves.
There are several ways to protect computers from cryptojacking, including using ad blockers, anti-malware software, and browser extensions that block mining scripts. It is also important to keep software up to date, avoid clicking on suspicious links or downloading unknown files, and monitor CPU usage for any unusual spikes. By taking these precautions, users can reduce the likelihood of falling victim to cryptojacking and safeguard their computers from potential harm.
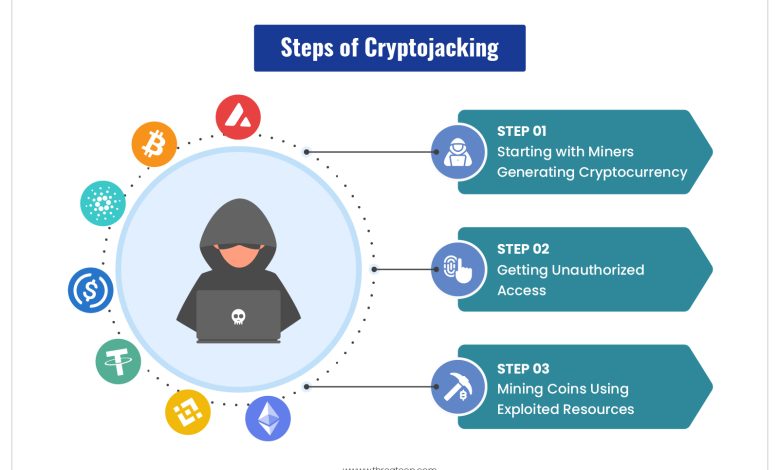
How Hackers Use Cryptojacking to Mine Cryptocurrency
Cryptojacking is a method used by hackers to mine cryptocurrency without the knowledge or consent of the device owner. This malicious activity involves installing malware on a victim’s computer, smartphone, or other internet-connected device to use its processing power to mine cryptocurrencies like Bitcoin or Monero.
One common way hackers use cryptojacking is by injecting malicious code into websites or online ads. When a user visits an infected website or clicks on a compromised ad, the code runs in the background without the user’s knowledge, using their device’s resources to mine cryptocurrency for the hacker.
Another method hackers use to cryptojack is by spreading malware through phishing emails or malicious downloads. Once the malware is installed on a device, it quietly mines cryptocurrency in the background, often slowing down the device and draining its battery.
Cryptojacking can have serious consequences for victims, including increased electricity bills, reduced device performance, and potential data breaches. To protect against cryptojacking, users should be cautious when clicking on links or downloading files from unknown sources and regularly update their security software to detect and remove any malicious code.
The Dangers of Cryptojacking for Individuals and Businesses
Cryptojacking poses significant risks for both individuals and businesses. For individuals, the main danger lies in the unauthorized use of their devices’ computing power to mine cryptocurrencies. This can lead to a slowdown in performance, increased electricity bills, and potential hardware damage. Additionally, cryptojacking can compromise personal data stored on the device, putting sensitive information at risk.
Businesses are also at risk of falling victim to cryptojacking attacks. When employees’ devices are cryptojacked, it can lead to decreased productivity and potential data breaches. Furthermore, if a business’s servers are compromised, it can result in significant financial losses and damage to the company’s reputation.
It is essential for both individuals and businesses to take proactive measures to protect themselves against cryptojacking. This includes using reputable antivirus software, keeping operating systems and software up to date, and educating employees about the risks of clicking on suspicious links or downloading unknown files. By staying vigilant and implementing robust cybersecurity measures, individuals and businesses can reduce the likelihood of falling victim to cryptojacking attacks.
Detecting and Preventing Cryptojacking Attacks
Cryptojacking attacks can be detrimental to individuals and organizations, leading to compromised systems and stolen resources. It is crucial to be proactive in detecting and preventing these attacks to safeguard against potential threats.
One effective way to detect cryptojacking activity is to monitor system performance for any unusual spikes in CPU usage. This can indicate that malicious software is running in the background, mining cryptocurrency without the user’s consent. Additionally, keeping an eye out for unauthorized access to systems or unusual network traffic can help identify potential cryptojacking attempts.
Preventing cryptojacking attacks involves implementing robust cybersecurity measures. This includes keeping software and security patches up to date to prevent vulnerabilities that attackers can exploit. Utilizing ad blockers and anti-cryptomining extensions in web browsers can also help block malicious scripts from running on websites.
Furthermore, educating employees and individuals about the risks of cryptojacking and the importance of practicing good cybersecurity hygiene is essential in preventing these attacks. By raising awareness and promoting a security-conscious culture, organizations can reduce the likelihood of falling victim to cryptojacking schemes.
Tools and Techniques to Safeguard Against Cryptojacking
Protecting against cryptojacking requires a combination of tools and techniques to safeguard your systems and devices. Here are some effective strategies to defend against this threat:
- Use ad-blockers: Ad-blockers can help prevent malicious ads from running scripts that could lead to cryptojacking.
- Install anti-malware software: Anti-malware programs can detect and remove cryptojacking scripts from your system.
- Keep software updated: Regularly updating your operating system and software can help patch vulnerabilities that cryptojackers exploit.
- Monitor system performance: Keep an eye on your system’s performance for any signs of unusual activity that could indicate cryptojacking.
- Implement network monitoring: Utilize network monitoring tools to detect any unauthorized connections or traffic associated with cryptojacking.
- Use browser extensions: Browser extensions like NoCoin and MinerBlock can help block cryptojacking scripts from running in your browser.
By incorporating these tools and techniques into your cybersecurity strategy, you can reduce the risk of falling victim to cryptojacking attacks and protect your resources from being hijacked for cryptocurrency mining.
The Future of Cryptojacking: Evolving Threats and Security Measures
Cryptojacking is a constantly evolving threat in the world of cybersecurity. As technology advances, so do the methods used by cybercriminals to mine cryptocurrencies using other people’s devices without their knowledge. To stay ahead of these evolving threats, it is crucial for individuals and organizations to implement robust security measures.
One of the most effective security measures against cryptojacking is to use ad blockers and anti-cryptomining extensions on web browsers. These tools can help detect and block malicious scripts that are used for cryptojacking. Additionally, keeping software and security patches up to date can help prevent vulnerabilities that cybercriminals exploit for cryptojacking.
Another important security measure is to educate users about the risks of cryptojacking and how to recognize signs of a potential attack. By raising awareness and promoting good cybersecurity practices, individuals can protect themselves and their devices from falling victim to cryptojacking.
Furthermore, organizations can implement network monitoring tools to detect unusual activity that may indicate cryptojacking. By monitoring network traffic and behavior, IT teams can identify and respond to cryptojacking attacks in a timely manner, minimizing the impact on their systems and data.
In conclusion, the future of cryptojacking poses significant challenges for cybersecurity, but with the right security measures in place, individuals and organizations can effectively protect themselves against this evolving threat. By staying informed, using security tools, and promoting cybersecurity awareness, we can all contribute to a safer digital environment.



